Key takeaways
- India first compliance requires alignment with the DPDP Act, the IT Act and Rules, RBI cyber and fraud guidance, GST and Income Tax provisions, MCA record keeping, and Cert In directions.
- Protect payroll, GST, TDS, vendor KYC, bank reconciliations, and ledgers with access control, encryption, logging, and clear retention, blend accounting discipline with security discipline.
- A CA led virtual accounting model, such as AI Accountant, embeds maker checker, structured repositories, and audit trails, reducing penalties and breach risk while improving efficiency.
- Adopt a practical roadmap and a monthly checklist, centralize documents, turn on MFA, standardize reconciliations, and keep proofs mapped to each filing.
- Use focused KPIs, on time filing, recon completion, access reviews, MFA coverage, and retention compliance, to demonstrate control during audits.
Introduction to Compliance for Financial Data Security
Compliance for financial data security means following the law and using strong controls so financial data remains confidential, correct, and available. Think payroll, GST filings, TDS records, vendor KYC, bank reconciliations, and ledgers, these demand protected storage, proper access, and clear logs that show who did what and when.
Why this matters now in India is clear. The DPDP Act allows very large fines for weak safeguards, breaches can reach up to two hundred and fifty crore rupees. Beyond fines, a data leak or failed audit damages trust with clients, blocks new deals, and can disrupt operations. GST and Income Tax audits expect strong records and proof of control, so this is not just a tech job, it is an operations job that blends accounting discipline with security discipline.
Practical compliance is a daily workflow, not a one time policy. Controls must live inside bookkeeping, reconciliations, filings, and reviews.
This India first guide draws on the DPDP Act, the IT Act and Rules on reasonable security, RBI cyber and fraud guidance, MCA and GST rules, and Cert In directions about logs stored in India. If you serve overseas clients, add a light view of GDPR or CCPA basics, consent and data minimization. Virtual accounting services can help bring all of this into daily work. Learn how a CA led virtual model supports financial data security.
Sources: DLA Piper, India Data Protection, CAPCO, DPDP Act overview, NLR, India compliance trends, Resecurity, RBI compliance
Regulatory Landscape in India for Compliance for Financial Data Security
DPDP Act 2023
Use reasonable security safeguards for personal data, including payroll and vendor KYC. Apply encryption, access control, and logging. If you are a Significant Data Fiduciary, plan Data Protection Impact Assessments, audits, and periodic reviews.
IT Act and Rules on Reasonable Security Practices
Protect data with standard measures, process checks, technical controls, and audit logs for key financial transactions.
RBI Cybersecurity and Fraud Frameworks
Regulated entities need board approved cyber policies, live monitoring, and fast incident reporting. Even if you are not a bank, borrow these good practices. Digital lending rules push for data localization in payments, and the Fraud Risk Management direction expects strong audit trails.
GST, Income Tax, Companies Act Retention and Reporting
Retain GST invoices generally for seventy two months from the due date of the annual return for the year. Income Tax records often run six years or more. Maintain MCA registers and minutes safely as required. TDS reporting needs complete proofs such as challans and returns like Form 24Q and Form 26Q.
Cert In Directions 2022
Keep logs for financial transactions and store them in India for set periods to support detection and response.
Payments and PCI DSS
If you handle card data, implement PCI DSS controls. RBI also asks certain payment data to be stored in India.
Use this map as a working checklist, ask a CA led virtual accounting partner how they meet these items through process design, secure storage, and audit trails.
Sources: CAPCO, DPDP Act overview, DLA Piper, India Data Protection, Resecurity, RBI compliance, NLR, India compliance trends, PwC, regulatory developments
Global Data Compliance Touchpoints for Cross Border Work
Data minimization
Only collect and store what you need, if a field is not required, do not store it.
Consent and transparency
Explain how you use data and obtain clear consent when required. Larger clients may ask for ISO 27001 or SOC 2. Even without certification, adopt core habits, access reviews, encryption, change control, and continuous monitoring.
Source: CAPCO, DPDP Act overview
Core Pillars of Compliance for Financial Data Security
Governance and Risk Assessment
Create a data inventory. Map flows, owners, and access. If you are a Significant Data Fiduciary, plan a DPIA. Review risks quarterly and track fixes.
Access Control and Least Privilege
Grant only needed access, enable multi factor authentication, review access quarterly, keep logs and alert on unusual access.
Secure Data Handling
Classify data as public, internal, confidential, or restricted. Use protected sharing for PII and financial records, block unapproved sharing.
Encryption and Masking
Encrypt data in transit and at rest. Mask sensitive fields in reports when full values are not required.
Logging and Audit Trails
Keep event logs for access, changes, and key actions. Maintain audit trails for bank reconciliations, ledger edits, and filings.
Vendor Management and Contracts
Run due diligence, sign data processing terms that cover security, breach notice, and deletion or return of data.
Business Continuity and Backups
Back up accounting and documents, test recovery often, keep an offsite or cloud copy in India where localization applies.
Incident Response
Write a simple playbook, define who to alert, how to contain, and how to report to the Data Protection Board if required, test yearly.
Retention and Deletion
Create a retention matrix. For example, keep GST records at least seventy two months, Income Tax records around six years or more. See a practical retention guide.
Training and Continuous Monitoring
Train staff and vendors on e invoice handling, TDS data care, and DPDP basics. Run internal audits and vulnerability checks, fix issues fast.
Sources: CAPCO, DPDP Act overview, DLA Piper, India Data Protection, Resecurity, RBI compliance, NLR, India compliance trends
Map Compliance for Financial Data Security to Daily Accounting Work
Bookkeeping and Ledgers
Use maker checker for entries and edits, post monthly close sign off notes, keep an audit trail for all journal changes, run integrity checks for outliers.
Reconciliations
Separate duties. One person prepares, another reviews and closes. Keep evidence and exception logs, clear within thirty days.
GST Filings
Control e invoice processes, maintain RCM documentation, map HSN codes and rates, keep proofs for GSTR 1 and GSTR 3B filings with working papers and acknowledgments.
TDS and Income Tax
Validate PAN data, track challans and BSR codes, keep proofs for returns like 24Q and 26Q, track Form 16 issuance and delivery.
Payroll
Handle personal data with DPDP grade care, restrict access, encrypt payslips at rest and in transit, log access to payroll records.
ROC and MCA
Keep statutory registers and minutes in a secure repository with version history and controlled access.
Documents and Communication
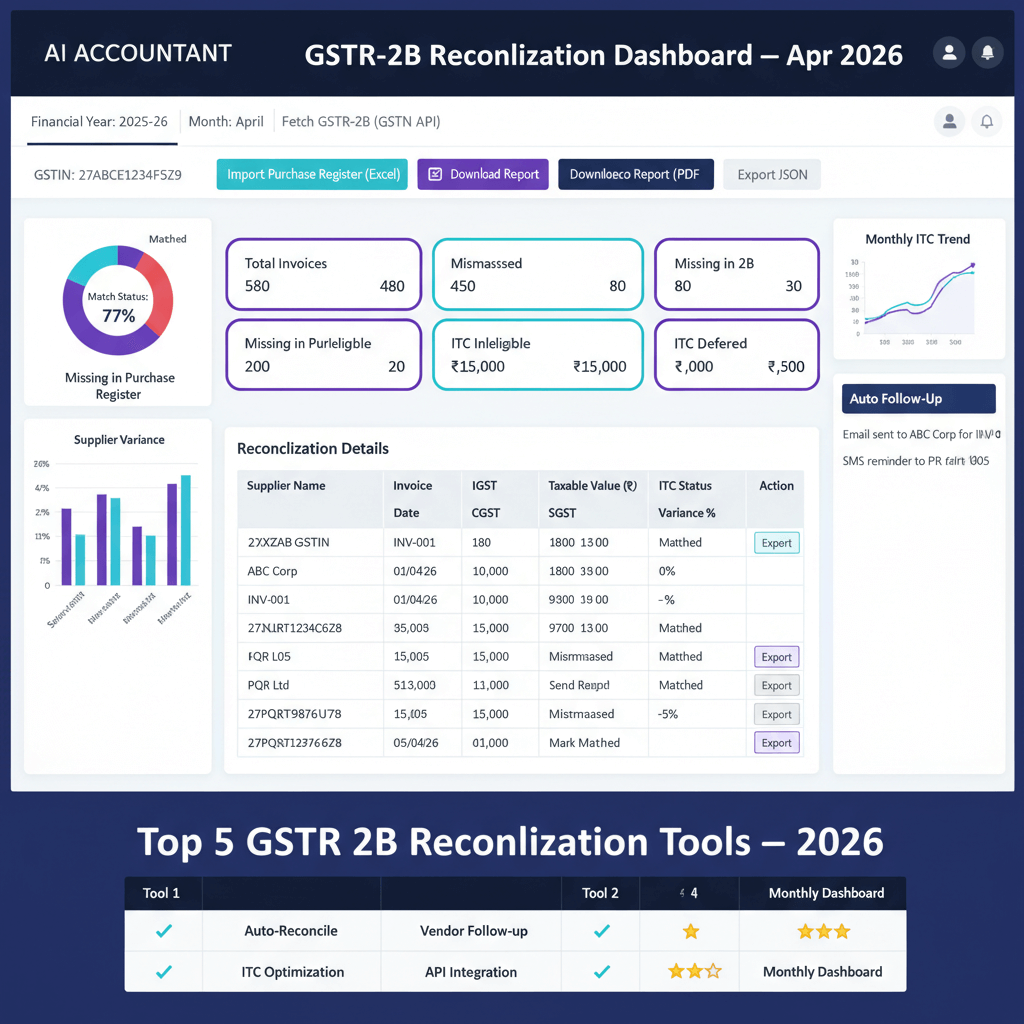
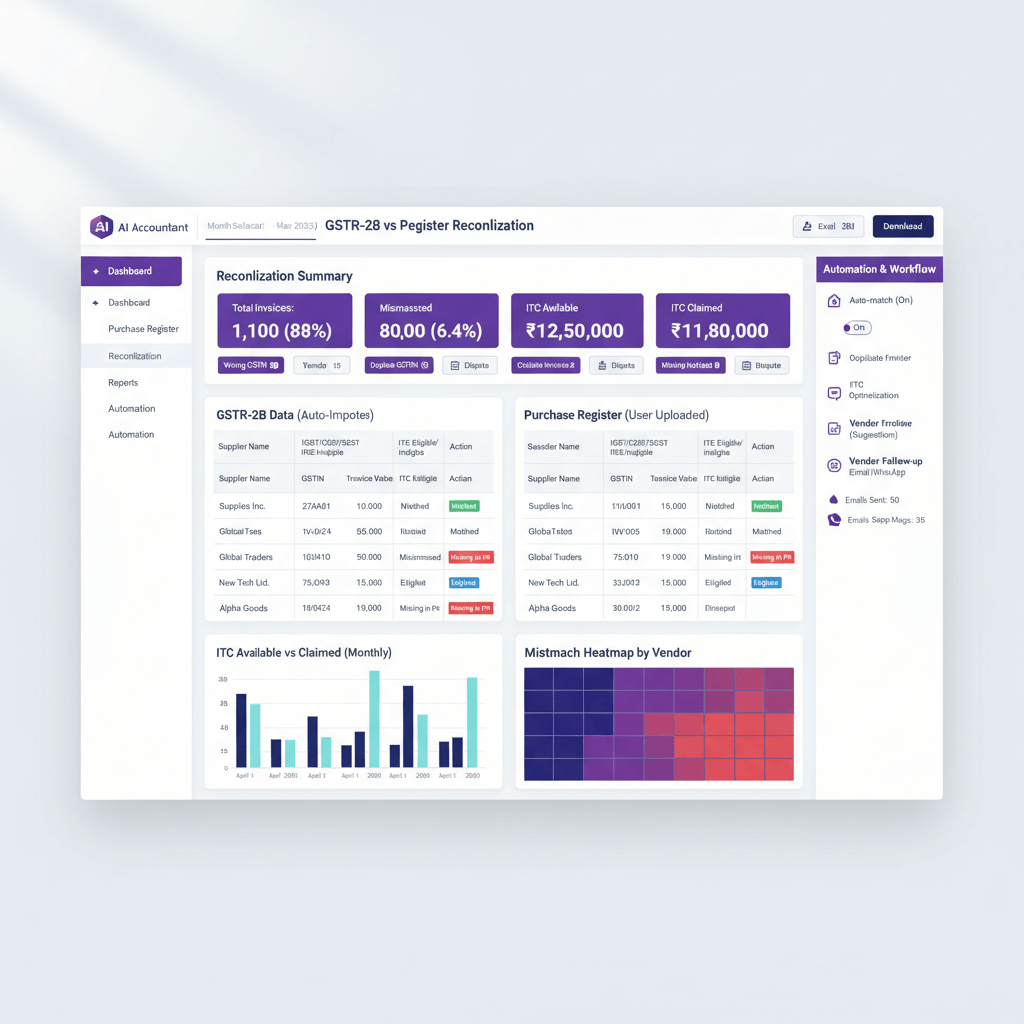
Use a central document store with version control and access logs, avoid scattering data in email or chat. A secure dashboard with your CA team reduces leak risk and speeds audits.
Sources: Resecurity, RBI compliance, NLR, India compliance trends, DLA Piper, India Data Protection, CAPCO, DPDP Act overview
How Virtual Accounting Supports Compliance for Financial Data Security
CA led processes
Monthly bookkeeping, reconciliations, and year end closes run with maker checker. Each step creates an audit ready trail, and the CA team coordinates with statutory auditors so evidence is complete and tidy.
Secure dashboard
View revenue, expenses, cash, burn, and runway, track GST, TDS, Income Tax, and MCA calendars, monitor filing status, and store documents in a structured repository. AI insights flag trends and possible issues early. Access is controlled and logs are retained.
Impact
You reduce penalties and lower breach risk, you align with DPDP and RBI style expectations without hiring a full in house team, and you replace scattered spreadsheets and emails with a managed system.
Sources: Resecurity, RBI compliance, NLR, India compliance trends, CAPCO, DPDP Act overview
Implementation Roadmap for Startups, SMEs, and Freelancers
- Baseline, list your data, map flows for payroll, GST, TDS, and sales, note personal data fields, do a gap assessment against DPDP, the IT Act, RBI ideas, and client asks, plan a DPIA if you are a Significant Data Fiduciary.
- Centralize, pick one system for books, documents, and compliance calendars, a virtual accounting dashboard helps, see cloud based financial operations.
- Define roles and MFA, set roles, approvals, and maker checker, enable MFA across all finance tools.
- Configure calendars and alerts, set due dates for GSTR 1, GSTR 3B, TDS, advance tax, ITR, and ROC forms, add reminders and escalation paths.
- Standardize templates and retention, create templates for invoices, e invoice data, RCM memos, TDS working papers, and recon packs, build a retention matrix tied to law.
- Run monthly reconciliations, close bank and gateway recon each month, age and track exceptions, target closure within thirty days.
- Write incident and vendor procedures, define breach response and vendor due diligence, maintain a current vendor list and signed DPAs.
- Train teams, run short training on DPDP basics, e invoice controls, TDS accuracy, and secure sharing, repeat every six months.
- Hold quarterly reviews with your CA, check access logs, recon status, filing on time rates, and exceptions, agree next actions.
- Improve using dashboard feedback, use AI alerts and trend views to refine controls, adjust roles and thresholds as you scale.
Sources: CAPCO, DPDP Act overview, DLA Piper, India Data Protection, NLR, India compliance trends, Resecurity, RBI compliance
Practical Checklist for Compliance for Financial Data Security
- Enable MFA on all finance and document tools
- Maintain a single secure repository with access control and version history
- Stop uncontrolled shares and public links
- Keep monthly reconciliation evidence and sign offs
- Map filing proofs to each return number and payment
- Use a retention matrix that covers GST, Income Tax, and ROC
- Maintain a vendor list and signed DPAs
- Test your incident playbook once a year
- Run quarterly access reviews and fix gaps
- Keep an active compliance calendar with alerts and owners
Sources: DLA Piper, India Data Protection, CAPCO, DPDP Act overview, Resecurity, RBI compliance
Recommended Accounting Tools that Support Data Security and Compliance
- AI Accountant, a CA led virtual accounting service with a secure dashboard for books, GST, TDS, Income Tax, payroll, and ROC support, includes a document repository, compliance calendar, AI insights, and controlled access, visit AI Accountant.
- QuickBooks Online, cloud accounting with user roles, audit logs, and bank feeds.
- Xero, cloud ledgers with advanced reconciliation and user permissions.
- Zoho Books, India friendly GST features, role based access, and workflows.
- Tally Prime, popular in India with strong inventory and GST support when paired with secure backup and access policies.
- FreshBooks, simple invoicing and expense tracking for freelancers and small teams.
- Sage Intacct, mid market financial management with strong controls and reporting.
No tool is perfect, how you set access, structure approvals, and keep evidence matters most.
KPIs and Evidence to Prove Compliance for Financial Data Security
- On time filing rate, target one hundred percent for GST, TDS, Income Tax, and ROC, keep dashboard logs and acknowledgments.
- Reconciliation completion, target one hundred percent monthly, maintain exception logs and close items within thirty days.
- Access reviews, target zero overdue reviews each quarter, keep a signed review note and change list.
- MFA enablement, target one hundred percent of users on all finance and storage tools, keep screenshots or system reports.
- Audit query turnaround, target closure under seven days, track dates and outcomes.
- Retention compliance, target one hundred percent records tagged with the right hold time, keep a retention matrix and samples.
Sources: Resecurity, RBI compliance, NLR, India compliance trends, CAPCO, DPDP Act overview, DLA Piper, India Data Protection
Common Pitfalls and How to Avoid Them in Compliance for Financial Data Security
- Scattered data in email or chat, move to a central dashboard and repository with access control.
- No maker checker for entries and filings, add approvals and role based steps for key actions.
- Ignoring DPDP in payroll, classify payroll as personal data, encrypt storage and sharing, restrict access, and keep logs.
- Weak RCM or HSN documentation, maintain memos and working papers that show decisions and rates.
- Delayed reconciliations, use automated reminders and a monthly close calendar, review exceptions weekly.
Sources: CAPCO, DPDP Act overview, DLA Piper, India Data Protection, Resecurity, RBI compliance, NLR, India compliance trends
Closing Thoughts on Compliance for Financial Data Security
Compliance for financial data security is a daily habit inside bookkeeping, reconciliations, GST and TDS filings, payroll, and ROC work. When you add access control, logs, encryption, and clear retention, you protect your business, and you save time in every audit.
You do not need a large in house team to reach this level. A CA led virtual accounting service like AI Accountant brings structure, visibility, and control through one dashboard and a dedicated team. Start with three steps, list your data, centralize tools, and turn on MFA, then add maker checker and monthly reconciliations. With that base, the rest becomes much easier.
FAQ
What is the difference between security and compliance for finance teams in India
Security is about safeguards, encryption, access control, logging, and monitoring. Compliance is about meeting laws like the DPDP Act and IT Act, proving this with policies, evidence, and audits. A CA led model such as AI Accountant ties these together by embedding controls in bookkeeping and filings while maintaining audit ready proof.
Do freelancers and sole proprietors really need DPDP grade controls for client data
Yes, if you handle personal or financial data you fall under the DPDP Act and the IT Act. You can keep it simple, centralize documents, enable MFA, restrict shares, and keep clear logs. An AI enabled Virtual Accounting partner can provide a secure portal and workflows without heavy setup.
Which records must I retain, and for how long, to stay compliant during GST and Income Tax audits
Keep GST invoices generally for at least seventy two months from the due date of the annual return for the year, Income Tax records usually six years or more if assessments are pending, and MCA registers and minutes as per Companies Act requirements. Map each record type in a retention matrix and store proofs in a version controlled repository.
How does an AI enabled Virtual Accounting model like AI Accountant help with DPDP readiness
It offers role based access, MFA, encryption at rest and in transit, document classification, maker checker workflows, and immutable activity logs. This supports DPDP expectations for reasonable security safeguards and creates evidence you can share during audits or with clients.
As a founder, what KPIs should I track monthly to prove control to my board and auditors
Track on time filing rate for GST, TDS, Income Tax, and ROC, reconciliation completion and exception aging, quarterly access review completion, MFA coverage, audit query turnaround times, and retention tagging coverage. A dashboard from AI Accountant can surface these KPIs with links to supporting documents.
For a CA firm managing clients, what segregation of duties is practical without adding headcount
Use maker checker on journals and filings, preparer and reviewer for reconciliations, and separate roles for vendor master changes versus payment approvals. A virtual accounting platform can automate routing and approvals so one person cannot initiate and approve the same action.
When do I need a Data Protection Impact Assessment under DPDP, and how do I scope it for finance processes
If you are a Significant Data Fiduciary or you process high risk personal data at scale, plan a DPIA. Scope it to payroll processing, vendor KYC, and any cross border transfers, evaluate risks in access, encryption, logging, and retention, and record the mitigations implemented in your finance systems.
How should I evaluate a Virtual Accounting or CA managed service provider for data security
Ask about MFA enforcement, encryption, access logs, data localization, maker checker workflows, vendor due diligence, and incident response. Request sample audit trails for a GST filing, a bank reconciliation, and a payroll run. AI Accountant can provide a demo repository with redacted proofs and activity logs.
We operate in India and serve EU or US clients, what minimum global controls satisfy GDPR or CCPA asks
Adopt data minimization, clear consent and notices, encryption at rest and in transit, quarterly access reviews, and a basic vendor DPA. If clients ask for ISO 27001 or SOC 2, align your policies and evidence first, then consider certification. Your virtual accounting team can maintain the evidence library for you.
If a suspected breach occurs in finance systems, what immediate steps should a finance head take
Contain access, rotate credentials, preserve logs, and notify your incident team. Assess scope, affected records, and whether DPDP reporting thresholds apply. Document the timeline, actions taken, and contact points. AI Accountant’s playbook includes role based alerts and a checklist to capture evidence.
Do we need PCI DSS if we only reconcile card settlements but do not store cardholder data
If you do not store, process, or transmit cardholder data, your PCI scope may be limited, however confirm with your payment provider and ensure your environment does not capture PAN or CVV in logs or exports. Keep strong access control and logging around gateways and settlement reports.
What is a practical budget and timeline to implement a baseline program for a 20 person startup
In four to six weeks you can centralize documents, enable MFA, define roles, implement maker checker, set the compliance calendar, and complete your first month end with full evidence. Costs are mostly platform subscriptions and a CA managed service retainer, often lower than a single full time hire.
How do I demonstrate reasonable security to enterprise clients during vendor onboarding
Share your data flow diagram, access policy, MFA coverage report, sample audit trails for filings and reconciliations, retention matrix, and incident playbook summary. A virtual accounting partner like AI Accountant can package these artifacts with redactions to speed vendor due diligence.
Can AI help detect accounting anomalies without breaching privacy
Yes, by using masked fields and aggregate signals, AI can flag duplicate invoices, unusual payment timings, or inconsistent HSN rates while protecting personal data. AI Accountant applies alerts on reconciliations and filings, and routes findings through maker checker for review.
How should freelancers share invoices and proofs securely with their CA
Use a secure portal with access control and version history, avoid email attachments and public links, enable MFA, and keep a monthly folder structure tied to filings. A lightweight virtual accounting workspace provides exactly this without complex setup.
-01%201.svg)