Key takeaways
- Row level security ensures users in CA firms and SMB finance teams see only the specific organizations, GSTINs, branches, ledgers, and transactions they are authorized to access.
- A solid user to entity mapping, deny by default policies, centralized approvals, and immutable audit logging are foundational to a successful rollout.
- India specific complexities, such as one PAN mapping to multiple GSTINs, varied branch codes across systems, and TAN based TDS flows, require careful modeling and testing.
- Enforce controls in the database layer for strongest security, complement with BI tool RLS for usability, validate end to end with synthetic users and CI integrated tests.
- Proper controls reduce breach risk, streamline audits, and simplifies ISO 27001 and SOC2 compliance while strengthening client trust.
Understanding Row Level Security in the Indian Context
Row level security restricts access at the individual record level, it draws invisible boundaries around each row so users only view data aligned to their role, entity, and scope. For Indian finance teams, this control is essential across multi entity engagements, complex GST structures, and outsourced operations.
What row level means for financial data
- Banking, control access to specific accounts, branches, and transactions per entity, each bank line item should be visible only to authorized users.
- GST, enforce GSTIN level access for purchase and sales registers, e-invoices, and reconciliations.
- Ledgers, apply granular controls across customer and vendor ledgers, payroll, director loans, and intercompany transactions.
- Dashboards, slice by organization ID, GSTIN, or branch so regional heads see their zone while CFOs maintain group wide visibility.
India specific complexity
Indian structures often map one PAN to multiple GSTINs across states, branch codes vary by system, and TDS datasets hinge on PAN, TAN, sections, and deductee types. Multi entity groups with subsidiaries, SPVs, and related party flows require careful hierarchy modeling. Outsourced processors need temporary, tightly scoped access without cross client leakage.
Technology stack considerations
- Source systems, Tally, Zoho Books, ERPNext, and bank imports provide baseline controls, but may lack row level precision.
- Data storage, Postgres, Snowflake, BigQuery, and data lakes support native row level enforcement, with varying feature sets.
- Analytics platforms, Power BI, Looker, Tableau, and Zoho Analytics offer RLS that complements database policies.
- File workflows, GST offline tools, Excel uploads, and CSV imports need special handling because files escape traditional row level controls.
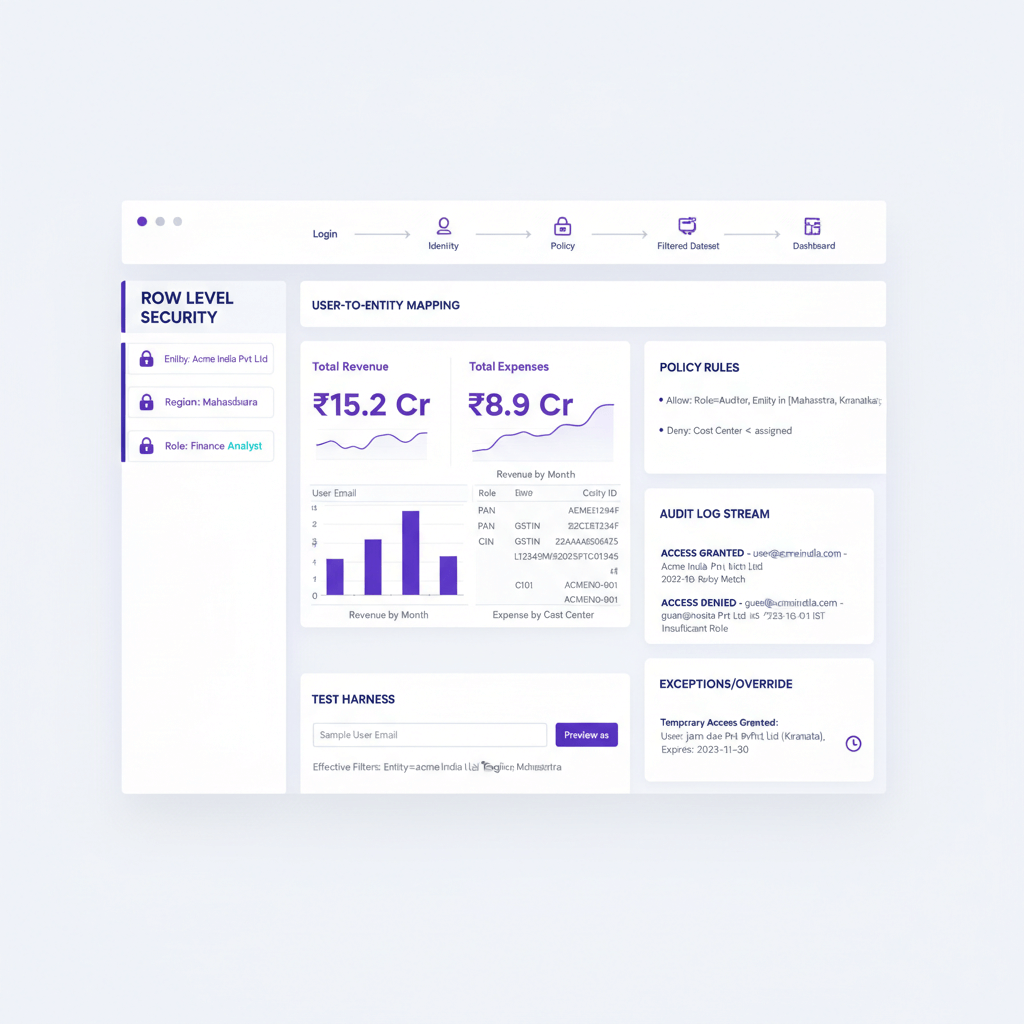
User to Entity Mapping Strategies
The mapping of users to entities is your single source of truth for access decisions, it determines who can see what, and under which scope.
Defining entities and users
Entities can be companies with client codes, specific GSTIN registrations, branches, warehouses, or business units like D2C versus B2B. Users span CA partners, managers, associates, article clerks, outsourced staff, and client finance roles like CFOs, controllers, and regional heads, auditors and consultants may need temporary access.
Mapping approaches
- Role based, assign portfolios by client or GSTIN to partners, seniors, and juniors.
- Attribute based, grant access where organization IDs or branch IDs match user attributes, this scales for complex groups.
- Group rollups, model hierarchies so holding company teams inherit subsidiary access, while regional shared services cover their geography.
Canonical mapping table design
Build a robust table with user ID, entity ID, and scope, include read, write, approve, and export permissions. Add data domains like GL, AP, AR, payroll, validity windows, approver ID, and reason fields. Keep full audit columns, created at, created by, revoked at, revoked by.
Managing shared services and cross entity access
Model shared service users with one mapping row per entity or through group expansions. Use read only scopes, disable exports, monitor more strictly, and set shorter validity periods.
Tip, cross entity access should be explicit, documented, and time bound.
Synchronizing with HR and practice management systems
Pull lifecycle events from HRIS and identity providers like Azure AD, Google Workspace, or Okta. Automate mapping creation on engagement start, updates on team changes, and revocations on last working day or engagement close. Nightly jobs should purge expired entries, trigger alerts for stale mappings, and enforce quarterly reviews.
Filter Policies and Implementation
Filter policies translate mappings into executable rules, they determine which rows are visible and enforce least privilege.
Understanding filter policies
Implement as SQL predicates in database RLS, DAX filters in Power BI roles, or row access policies in cloud warehouses. A common approach joins data rows to the mapping table, then applies a deny by default stance.
India specific filter examples
- GSTIN filters, restrict purchase and sales registers per GST registration.
- Organization ID, isolate multi company books by canonical entity ID.
- Branch and region, allow zonal managers to view only their locations.
- Ledger class, grant payroll ledgers to HR finance, restrict director loans to senior management and auditors.
Best practices for filter design
Adopt a deny by default posture, explicitly allow only the rows specified by approved mappings, and version control every policy change.
- Use positive allowlists, avoid denylists.
- Centralize policy definitions in SQL, YAML, Terraform, or dbt, log all changes.
- Design inheritance carefully for holding company and auditor scenarios.
Implementation layers
- Database layer, Postgres CREATE POLICY, Snowflake row access policies, BigQuery authorized views, strongest enforcement.
- BI layer, Power BI RLS with USERPRINCIPALNAME(), Looker user attribute filters, Tableau data source filters, great for quick wins.
- ETL and semantic layers, pre filtered marts for sensitive domains like payroll, still backed by RLS on source systems.
Building a Reliable Test Harness
A rigorous test harness validates policies before production, it catches configuration errors early and prevents incidents.
Synthetic data generation
Create 5 to 10 varied test entities, include single GSTIN SMEs, multi GSTIN groups, multi branch retail, and service firms with PAN only flows. Add branches, warehouses, cost centers, and dummy users across roles, partners, seniors, associates, CFOs, plant heads, auditors, and contractors.
Test categories
- Positive, users see assigned organization IDs, GSTINs, branches, and permitted ledgers.
- Negative, users cannot access other clients, unrelated GSTINs, other regions, or sensitive ledgers.
- Boundary, expired access, overlapping roles, and monitored break glass accounts.
- Data skew, mix very large and small entities, verify performance and UX for shared service users.
Automation and CI integration
Integrate RLS tests into CI, connect as synthetic users, run standard queries, assert row counts. Include sensitive rows like payroll and director loans, verify no leakage across joins.
Outcome, policy changes ship with confidence, regressions are caught automatically.
Audit of Access and Compliance
Immutable logs, regular reviews, and anomaly detection create strong evidence for audits, while protecting client confidentiality.
Logging requirements
Store immutable audit trails capturing user ID, entity ID, policy version, query or dashboard ID, row counts, timestamps, and declared purpose, such as monthly close or statutory audit. Use append only tables or WORM storage, restrict writers to the logging pipeline, apply RLS and column security on the logs themselves.
Review cadence and processes
- Weekly anomaly detection, spikes in row counts, first time access to new entities, off hours access.
- Monthly attestations, engagement owners and CFOs confirm access is still required.
- Quarterly internal audits, sample queries and align them to approved purposes.
Compliance alignment
SOC2 Type 2 and ISO 27001 rely on robust logging, least privilege, and regular reviews, India’s DPDP Act mandates purpose limitation, which your logs and policies should encode explicitly for payroll, KYC, and personal data domains.
Alert configuration
Enable real time alerts for bulk multi entity access by a single user, large extracts of sensitive ledgers, and unusual IP or geolocation patterns.
Exception Handling and Break Glass Procedures
Well designed break glass processes enable legitimate, time bound access during audits, year end close, or investigations, without compromising overall controls.
Break glass access design
Implement just in time, short lived privilege elevation, add temporary mapping rows or exception roles scoped to entities, ledgers, and duration, route approvals to CA partners or client CFOs, document justification and ticket references fully.
Compensating controls
- Enhanced logging for all exception sessions.
- Screen watermarking in BI dashboards, deter screenshots.
- Disable CSV, Excel, and PDF exports for exception users.
Emergency procedures
Maintain 24x7 deprovisioning for contractor offboarding or incidents, ensure last day access auto expires, remove across identity providers, practice tools, and mapping tables immediately.
Performance Optimization and Scalability
RLS can affect query performance, plan indexing, partitioning, and caching from day one.
Indexing and partitioning strategies
Create indexes on organization ID, GSTIN, branch ID, and user ID columns in fact and mapping tables. Partition large tables by organization ID, or by fiscal year plus organization ID, enable predicate pushdown to skip entire partitions.
Materialized views and caching
For large entities or low latency needs, create pre filtered materialized views by entity or group, maintain a global fact table as the source of truth. Pre compute aggregates by entity, month, and ledger class, ensure caches and cubes remain RLS aware.
Query optimization
- Replace large OR chains with joins to mapping tables or IN lists.
- Prefer numeric organization IDs over string comparisons.
- Monitor performance, tune indexes, and collaborate with DBAs while preserving security boundaries.
Common Pitfalls in the Indian Context
Data quality issues
- Mismatched or malformed GSTINs across systems, with spaces or formatting differences, break filters.
- Duplicate PANs or missing PAN to entity mappings cause incorrect visibility.
- Branch code drift across ERP, HR, and banking, MUM versus BOM, increases leakage risk.
Channel leakage points
Exports to Excel and CSV sent via email bypass controls, screenshots on WhatsApp or Slack leak sensitive data, shared generic logins destroy accountability.
Configuration mistakes
Over broad roles with no expiry, shadow data in local files, and unmanaged USB storage create silent risk. Mitigate with SOPs, DLP tools where feasible, and firm wide security awareness.
Step by Step Implementation Checklist
Phase 1, Inventory and planning
- List protected datasets, GL, AR, AP, bank statements, payroll, GST, TDS, working papers.
- Define entity boundaries, company, GSTIN, branch, business unit.
- Document current access, identify gaps versus desired posture.
Phase 2, Mapping and policy design
- Build the canonical mapping table with scopes, domains, and audits.
- Set approval workflows across partners, CFOs, controllers.
- Sync with HRIS and practice platforms for lifecycle automation.
- Draft database and BI predicates, version control them.
Phase 3, Technical implementation
- Choose enforcement layers per dataset risk.
- Implement high risk filters first, GL, payroll, bank, GST.
- Create a comprehensive test harness, cover positive, negative, boundary cases.
- Integrate tests with CI/CD for continuous validation.
Phase 4, Operational readiness
- Enable audit logging, monitoring, and anomaly detection.
- Schedule weekly checks and monthly attestations.
- Formalize break glass with compensating controls.
Phase 5, Training and rollout
- Document runbooks and SOPs.
- Train CA staff and client finance teams on access procedures.
- Run pilots with 2 to 3 entities, fix issues before scale.
Phase 6, Scale and optimize
- Roll out to full client base, embed in onboarding.
- Monitor performance and optimize based on usage.
- Iterate via audit findings and user feedback.
Tools and Platforms Supporting Row Level Security
- AI Accountant, built for Indian CA firms, multi entity RLS with Tally and Zoho Books integrations.
- Power BI, robust DAX based row level security for Microsoft centric teams.
- Snowflake, enterprise row access policies and secure data sharing.
- Postgres, native database RLS via CREATE POLICY.
- Tableau, user and data source filters for flexible visualization control.
- QuickBooks Online Advanced, suitable for smaller firms with basic permissions.
Practical Templates and Resources
User entity mapping table schema
Provide SQL DDL with lifecycle states, active, suspended, expired, revoked, include sample data for permanent employees, temporary contractors, and break glass scenarios.
Policy catalog template
Document entity, branch, and ledger level policies, define business rules, technical predicates, approval requirements, and exception steps.
Test case repository
Build positive, negative, and performance tests with expected outcomes, automate execution and reporting.
Audit log specification
Define mandatory fields, optional enrichment, retention periods by classification, and DPDP aligned purpose codes, include sample queries for user specific access reviews, entity access over time, and anomaly detection.
Integration with Modern Financial Automation
As bank feeds, GSTN integrations, and AI assistants expand, RLS must remain the guardrail. Multi entity rollups, CA multi org setups, and automated dashboarding should honor user mapping and filter policies. One click syncs with Tally and Zoho Books need correct filters, AI powered reconciliation should analyze global patterns while surfacing results only for authorized entities.
Result, automation scales safely, without eroding data boundaries.
Measuring Success and ROI
- Security, fewer unauthorized access incidents, faster detection and response, stronger audit findings.
- Operations, reduced manual access work, faster onboarding, fewer access tickets.
- Business, higher client confidence and retention, ability to handle complex multi entity engagements, competitive differentiation.
Quantify ROI by comparing implementation costs to avoided breach costs, reduced audit fees, productivity gains, and new business enabled by stronger security.
Future Proofing Your Implementation
Design for change, prepare for data localization, growing automation in GST and TDS, zero trust patterns, and vendor agnostic architectures. Keep portability in mind, avoid lock in to narrow tool features, and document decisions thoroughly.
Conclusion
Row level security in India is a core control for CA firms and SMB finance teams, it protects complex multi entity books, enables compliance, and builds trust. Start with clean user to entity mapping, implement rigorous filters, invest in a comprehensive test harness, and maintain strong audit trails with clear exception handling. Treat RLS as an ongoing discipline, not a one time project, and use it as a business enabler that allows your teams to scale confidently while keeping data boundaries intact.
FAQ
How should a CA firm define the canonical entity model for RLS when one PAN maps to multiple GSTINs?
Use a canonical organization ID per legal entity, then attach child entities for each GSTIN. Policies should filter on organization ID first, then GSTIN, so group level roles can inherit appropriately while GST registration specific roles remain narrow. Tools like AI Accountant model parent child relationships cleanly, enabling CFOs to see consolidated views, while staff access only their assigned GSTINs.
What is the recommended deny by default predicate for Postgres row level security in multi entity finance data?
Join the fact table to a normalized user to entity mapping on organization ID, GSTIN, and optional branch ID, then return rows only when a valid, unexpired mapping exists. This approach enforces least privilege reliably, and it is portable across databases and BI tools. In practice, AI Accountant ships with prebuilt policies that adopt this stance.
How can we ensure auditors get temporary read only access without export permissions during statutory audits?
Create an exception role scoped to specific entities and ledgers, set short validity windows, disable CSV and PDF exports in BI, and flag sessions with enhanced logging. Maintain approvals routed to engagement partners and CFOs, and verify logs post audit for misuse. Platforms like AI Accountant support such break glass workflows out of the box.
What is the best way to handle file based workflows like GST offline tools and CSV imports without breaking RLS?
Use secure collection portals, encrypt at rest and in transit, and import into controlled zones immediately, then enforce RLS in the warehouse or application. Avoid emailing files or storing them in unmanaged shares, prefer audited upload channels such as a secure document collection portal with immutable logging.
Can Power BI RLS alone be considered sufficient, or should we also enforce policies at the database layer?
For sensitive domains like payroll and director loans, enforce at the database layer first, then supplement with Power BI RLS. Database enforcement is the strongest boundary, it protects all downstream tools. BI RLS improves usability and is vital for curated dashboards, but it should not be the only control for high risk data. AI Accountant combines both approaches.
How do we audit purpose limitation in line with India’s DPDP Act for payroll and KYC datasets?
Log declared purposes per session or job, monthly close, statutory audit, investigation, then validate queries against those purposes. Store immutable audit trails with user ID, entity ID, row counts, and purpose codes. Review anomalies weekly, attest monthly, and sample quarterly, this approach meets DPDP expectations.
What indexing and partitioning strategy improves performance for RLS where some entities have millions of rows?
Index organization ID, GSTIN, branch ID, and join keys on mapping tables, partition large facts by organization ID, or by fiscal year plus organization ID. Predicate pushdown allows the engine to skip entire partitions before applying RLS filters, which keeps latency low even as data grows. Many AI Accountant deployments use this pattern.
How do shared service teams work across multiple clients without compromising data boundaries?
Model each client explicitly in the mapping table with separate rows per entity, restrict scopes to read only, prohibit exports, and set shorter validity. Monitor access patterns with anomaly detection and require quarterly attestations by engagement owners. This keeps cross client leakage in check while maintaining operational efficiency.
What controls prevent leakage via screenshots, WhatsApp, or emailed spreadsheets?
Combine process controls with technical measures, watermark BI screens during audits, disable mass export for sensitive domains, adopt SOPs that forbid uncontrolled shares, and implement DLP where feasible. The most effective defense is prevention, keep data inside RLS enforced apps, for example dashboards in AI Accountant with export constraints.
How should a CA practice synchronize access with HR and identity providers during onboarding and offboarding?
Automate provisioning via Azure AD, Google Workspace, or Okta signals, create mappings on engagement start, update on team reassignment, and revoke on last day. Run nightly jobs to purge expired entries and alert for stale access. Maintain a deprovisioning runbook for urgent removals that operates across identity, practice tools, and mapping tables simultaneously.
What test cases are mandatory before shipping any RLS policy change?
Positive tests for authorized visibility, negative tests for unauthorized blocks, boundary tests for expired and overlapping roles, and performance tests for skewed entity sizes. Execute as synthetic users inside CI, assert row counts for known scenarios, and include sensitive joins to validate no leakage.
How do we measure ROI for RLS in a CA firm serving 50 to 100 plus clients?
Track reduced unauthorized incidents, faster detection and response, improved audit scores, lower access management effort, and faster onboarding. Include business outcomes, client retention, ability to accept complex engagements, and competitive wins. Many firms see ROI through avoided breach costs and reduced audit effort in the first year.
Which tools offer out of the box RLS for Indian finance workflows?
Database first solutions like Postgres and Snowflake provide native enforcement, BI tools like Power BI and Tableau add dynamic filters, and specialized platforms like AI Accountant deliver multi entity RLS tailored for Tally and Zoho Books, with audit friendly workflows for CA practices.
-01%201.svg)