Key takeaways
- DPDP Act 2023 and DPDP Rules 2025 impose strict duties on CA firms, consent logging, breach notification within 72 hours, purpose limitation, and confidentiality are now non negotiable
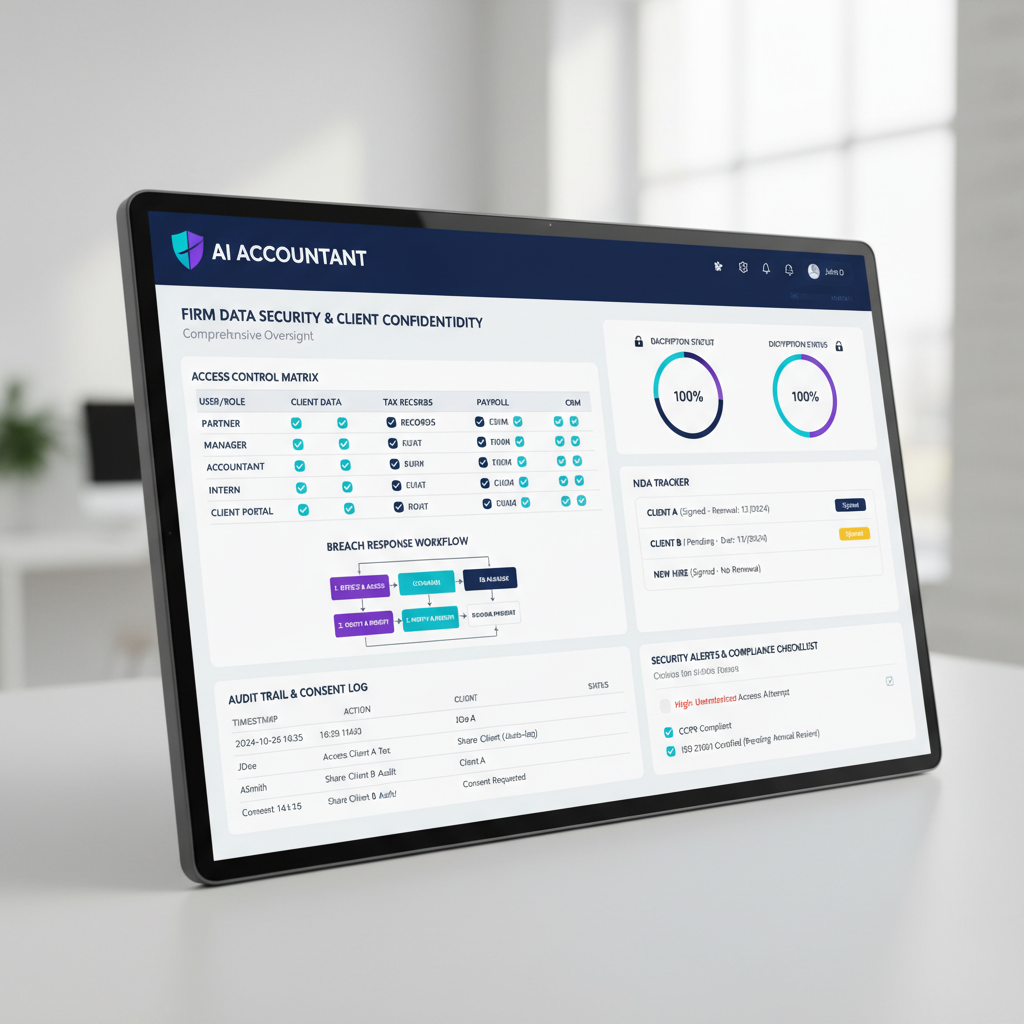
- A five pillar framework, access control by role, encryption, NDAs and engagement clauses, breach response, and consent logging, gives practical structure to secure client financial data
- A 90 day roadmap delivers quick wins, MFA and full disk encryption in week one, secure file sharing in week two, legal foundations and consent logs in week three, and access inventory in week four
- Replace email and WhatsApp attachments with secure client portals, use expiry links, watermark downloads, and keep audit trails
- Adopt tools with ISO 27001 and SOC 2 Type 2 certifications, prioritize AES 256 at rest and TLS 1.2 or higher in transit, and insist on granular RBAC, MFA, and SSO
- Build a security first culture, leadership commitment, monthly awareness training, transparent client communication, and quarterly audits turn security from crisis management into a competitive advantage
Why Data Security for CA Firms Matters More Than Ever
Data security for CA firms is mission critical in 2025, with the DPDP Act 2023 and the final rules now enforced. You are handling bank statements, GST returns, PAN data, payroll registers, and audit papers every day, which means you are trusted with highly sensitive personal and financial information. A single breach can trigger penalties up to ₹250 crore, and worse, it can erode decades of reputation.
The New Regulatory Landscape
The DPDP regime mandates explicit consent before processing personal data, timely breach notification within 72 hours, strict confidentiality, and purpose limitation. These are legal obligations backed by penalties. ICAI’s Code of Ethics aligns with these expectations and recent guidance emphasizes robust IT controls for cloud use and outsourcing. For orientation, see the DPDP Rules 2025 compliance overview, the SISA analysis of India privacy laws 2025, and ICAI guidance reported by The Accountant.
The Real Cost of Poor Security
Stolen laptops, misdirected emails, or lingering access for former employees all damage trust. Word spreads, clients begin to hesitate, new prospects stall, and penalties under DPDP compound the pain. The deeper cost comes from lost business and reputational harm that takes years to repair, as highlighted in the SISA analysis.
Understanding Your Data Landscape
CA firms process financial documents, tax records, identity information, business data, and working papers. These qualify as personal data under Indian law, bringing full DPDP compliance into scope. For clarity on covered data and obligations, refer to the India Briefing explainer and the JD Supra note on the final rules.
Common Security Gaps in CA Practices
WhatsApp file sharing, unencrypted USB drives, bank statements sitting in inboxes, and shared Tally credentials create dangerous exposures. Attackers target CA firms because the data is valuable and controls are often inconsistent.
The 5-Pillar Security Framework for CA Firms
Pillar 1, Access Control by Role
Use role based access control, partners, managers, seniors, article assistants, and bookkeeping staff get only the data they need. Implement unique logins, audit trails, and a joiner mover leaver process. Review access quarterly and remove unused permissions. Demand RBAC, MFA, SSO, detailed logs, and IP restrictions from vendors. For legal and operational alignment, see the DPDP overview and JD Supra guidance.
Pillar 2, Encryption at Rest and in Transit
Use AES 256 for data at rest and TLS 1.2 or higher for data in transit. Enable full disk encryption on all laptops with BitLocker or FileVault, ensure mobile devices are encrypted, and disable USB write access on sensitive workstations. Replace email attachments with secure client portals or expiry links, add watermarks to downloads for traceability.
Vet vendors for SOC 2 Type 2 or ISO 27001, ask about key management, encryption algorithms, and data residency, ideally India data centers. For deeper context, read the EY assessment of DPDP rules alongside the India Briefing overview.
Pillar 3, NDAs and Engagement Clauses
Use NDAs and engagement letters with confidentiality obligations, purpose limitation, retention and deletion terms, breach notification aligned to 72 hours, sub processor transparency, Indian jurisdiction, and explicit DPDP compliance. Maintain a clause library, track renewal dates, map agreements to employees, contractors, vendors, and clients.
Pillar 4, Breach Response Plan
Define what constitutes a breach, unauthorized access, lost devices, misdirected emails, compromised credentials. Build a RACI chart, evidence collection procedures, regulatory and client notification templates, and practice quarterly tabletop exercises. Document incidents and lessons learned for continuous improvement. See the DPDP overview, the final rules summary, and the EY insights.
Pillar 5, Consent Logging
Create a consent register linking to client files, track who consented, for what purposes, which data categories, retention period, sub processors, and withdrawal rights. Build checks into workflows before uploading bank statements or GST data, set reminders for expiry, and automate prompts during client onboarding. For policy context, see the DPDP overview and PwC regulatory update.
Implementation, Your 90-Day Roadmap for CA Firm Security
Days 0 to 30, Quick Wins for Immediate Impact
- Week 1, enable MFA on email and accounting systems, activate full disk encryption, deploy a password manager firm wide
- Week 2, stop email attachments for sensitive files, configure secure sharing in Microsoft 365 or Google Workspace, train the team on new processes
- Week 3, finalize NDA and engagement letter templates with DPDP clauses, start your consent log, identify gaps in legacy agreements
- Week 4, inventory access and data locations, list all software, identify shared logins, and document where client data resides, cloud, local, devices
Days 31 to 60, Process and Tooling Enhancement
- Weeks 5 to 6, define roles and access matrices, implement RBAC in email, storage, and accounting systems, remove unnecessary permissions
- Weeks 7 to 8, move fully to secure file exchange, add watermarking and link expiry, stand up client portals
- Week 8, write your breach response plan, run a tabletop drill, update procedures and role assignments
Days 61 to 90, Audit and Continuous Improvement
- Weeks 9 to 10, conduct internal security audit, remove stale access including former employees, test controls, and prioritize remediations
- Week 11, vendor due diligence, request certifications, verify encryption, and update agreements
- Week 12, document procedures, automate consent prompts, implement retention and deletion, and schedule quarterly reviews
Choosing the Right Security Tools for Your CA Practice
Essential Security Software Categories
Accounting automation tools should include strong security, granular RBAC, MFA, encryption, and audit trails. Consider these, AI Accountant AI Accountant, designed for Indian CA firms, with ISO 27001 and SOC 2 Type 2, bank statement automation, and DPDP aligned data handling, QuickBooks, Xero, Zoho Books, Tally Prime, and FreshBooks.
Password managers, Bitwarden or 1Password for small teams, business plans for mid size firms with shared vaults and policy controls, enterprise tiers for large firms with SSO and audit reporting.
Secure file sharing platforms, Microsoft SharePoint for Office 365 users, Google Drive for Workspace, and specialized platforms like Citrix ShareFile or Box for watermarking and remote wipe.
Vendor Due Diligence Checklist
- Access control, RBAC, SSO, MFA, and detailed logs
- Encryption, AES 256 at rest and TLS 1.2 plus in transit
- Legal protections, DPDP clauses, retention, and breach terms
- Incident response, documented playbook and 72 hour notification readiness
- Consent management, purpose, retention, withdrawal tracking, and deletion options
- Certifications, ISO 27001 and SOC 2 Type 2, plus regular penetration tests
- India context, GST, Tally, Zoho integrations, and India data residency
Integration Considerations
Prefer tools that integrate with Microsoft 365 or Google Workspace, use APIs to automate workflows while preserving security, and weigh total cost of ownership including training and administration. Integration reduces gaps and simplifies compliance.
Common Security Pitfalls and How to Avoid Them
The WhatsApp Trap
WhatsApp is convenient but risky for sensitive documents, devices store message history unencrypted at rest, there is no compliance audit trail. The fix, move clients to secure portals and business communication tools with access controls and logs.
Shared Login Syndrome
Shared credentials remove accountability and complicate investigations. Create individual accounts immediately, enforce MFA and password managers, and monitor logs.
Offboarding Amnesia
Former staff retaining access is common. Use an offboarding checklist, revoke all system access, collect devices and keys, and verify completion with reminders.
Unencrypted Backup Blindness
Encrypt backups with AES 256, store media securely, test restores regularly, and maintain a backup inventory. Unencrypted backups are a liability, not a safeguard.
Stale NDA Syndrome
Track NDA renewals, link agreements to counterparties, review annually, and update templates for regulatory changes. NDAs should reflect current services and data flows.
India-Specific Security Considerations
DPDP Act 2023 Compliance Requirements
Obtain informed consent, honor purpose limitation, report breaches within 72 hours, and enable data principal rights, access, correction, erasure, and portability. For a clear overview see the DPDP Rules 2025 explainer, the SISA overview, and JD Supra’s final rules summary.
GST and Banking Data Security
GST returns and bank statements reveal operations and financial histories, encrypt at rest and in transit, limit access by client account, and use India specific tools that understand local formats and sensitivities.
ICAI Professional Standards
ICAI expects confidentiality and robust IT controls, including encryption, access management, and secure disposal. Outsourcing requires clear arrangements, responsibility remains with the CA firm. See coverage by The Accountant.
Cross-Border Data Transfer Restrictions
Know where data resides, prefer India data residency to simplify compliance and performance, and when transfers abroad are unavoidable, add safeguards, stronger encryption, explicit consent, and contractual protections.
Building a Security-First Culture in Your CA Firm
Leadership Commitment
Security starts with partners. Discuss security in team meetings, invest in tooling and training, use strong passwords, follow secure processes, and create safety for reporting issues. Visible leadership drives firm wide adoption.
Team Training and Awareness
Run monthly awareness sessions, focus on practical CA contexts, how to share files securely, spot phishing, and respond to lost devices. Bake security into onboarding and recognize team members who identify risks.
Client Communication
Explain security as client benefit, encrypted portals protect their data, audit trails increase transparency. Provide clear instructions, highlight certifications and practices, and communicate openly if incidents occur.
Continuous Improvement
Schedule quarterly reviews, monitor emerging threats, learn from incidents, and evolve controls as the firm grows. Security is a continuous journey, not a one time project.
Practical Templates and Tools
Access Control Matrix Template
- Partners, full access to all modules and client data, administrative rights
- Managers, access to assigned clients except payroll, read only to firm financials, approval rights
- Senior associates, full access to assigned audit clients, read only to tax clients
- Article assistants, read only to assigned sections, edit working papers under supervision
- Bookkeeping team, edit access to bookkeeping modules only, restricted to current period
- External auditors, read only to scoped audit data, time bound access, limited downloads
- Client CFOs, access only to their company data, read only to historical data
Sample NDA Clauses
Explicit Confidentiality, all information shared by either party, including financial data, business operations, and personal information, shall remain strictly confidential and shall not be disclosed to any third party without prior written consent.
Breach Reporting, any suspected or confirmed data breach must be reported to the affected party within 72 hours of discovery, with full details of the nature, scope, and remediation measures taken.
Retention and Deletion, data shall be retained only for the period necessary to provide agreed services plus any statutory requirement period, upon termination of services, all data shall be securely deleted within 30 days unless otherwise legally required.
Sub Vendor Transparency, any sub processors or third party vendors who may access confidential data must be disclosed in advance, with evidence of equivalent security and confidentiality agreements.
Jurisdiction and Compliance, this agreement is governed by Indian law, including the Digital Personal Data Protection Act 2023 and rules thereunder.
Breach Response Checklist, First 24 Hours
- Hours 1 to 2, contain, identify affected data, isolate compromised systems, secure physical areas, activate incident team
- Hours 2 to 6, assess, document facts, identify affected clients, collect initial evidence, begin root cause analysis
- Hours 6 to 12, communicate, notify management, prepare client drafts, consult legal, draft regulatory notices
- Hours 12 to 24, respond, send client notifications, file regulatory reports if required, implement immediate remediation, continue investigation
Consent Log Structure
- Client information, company and contact details
- Consent details, date, method, authorized person, scope
- Data categories, bank statements, GST returns, identity documents, tools authorized, geography limits
- Timeline, validity and retention period, renewal date, withdrawal if exercised
- Sub processing, third parties, purposes, international transfers approvals
- Audit trail, modifications, renewals, withdrawals, special conditions
Measuring Security Success
Key Security Metrics
- Access control, accounts versus employees, MFA coverage, time to revoke access after departure, review frequency
- Incidents, count per quarter, time to detect, mean time to respond and contain, percentage with root cause identified
- Compliance, clients with valid consent, NDAs up for renewal, audit findings closed, time to file DPDP notifications
- Training, completion rates, phishing simulation click rates, policy violations reported, security suggestions submitted
Regular Audit Schedule
- Monthly, critical system access audits, backup verification, patch status checks, consent log review
- Quarterly, comprehensive access review, breach response drill, vendor security updates, client feedback
- Annual, full security audit preferably external, policy and procedure updates, NDA template reviews, tool effectiveness assessment
Conclusion, Your Security Journey Starts Today
Security is now core to CA practice excellence. The DPDP Act sets clear expectations, clients demand protection, and ICAI reinforces professional rigor. Use the five pillar framework, follow the 90 day plan, adopt certified tools, and make security part of your culture. Start today, enable MFA, encrypt laptops, end shared passwords, and move sensitive exchange to portals. Perfect security does not exist, consistent improvement does, and that consistency protects clients, reputation, and growth.
FAQ
How should a mid size CA firm structure breach notification to meet DPDP within 72 hours, and what templates are essential?
Adopt a staged playbook, discovery and containment in the first two hours, initial assessment by hour six, stakeholder drafts by hour twelve, and client plus regulatory notifications before hour seventy two. Prepare three templates, client notice in plain language with facts and remediation, Data Protection Board notice with scope, categories, and timelines, and an internal update for partners and managers. Tools like AI Accountant can centralize evidence capture and timeline logs for audit readiness.
What is the minimum viable RBAC model for Tally or Zoho Books to separate audit teams from bookkeeping teams?
Create roles by function, partners full access, managers scoped client access and approvals, audit seniors read only to bookkeeping modules, bookkeeping team edit access only to bookkeeping data and current period, article assistants read only to assigned clients. Enforce unique logins, MFA, and review access quarterly. AI Accountant can integrate with Tally and Zoho to mirror role scopes and maintain audit trails.
Which consent fields are mandatory under DPDP for client financial data, and how do I capture withdrawals cleanly?
Record data principal identity, consent date and method, purposes, data categories, retention period, tools and sub processors, and withdrawal rights. Link consent to each processing activity, for example bank statement ingestion for tax, and log withdrawals with effective date, downstream deletion actions, and confirmation to the client. AI Accountant supports consent tags at the document level, simplifying withdrawal execution.
Is WhatsApp ever acceptable for client documents under DPDP, if we delete messages quickly?
It is not recommended for sensitive documents. Devices store content at rest, there is no audit trail, and link sprawl is unmanageable. Use secure portals with expiry links and watermarking, for example AI Accountant’s client portal workflows, and reserve WhatsApp for scheduling or non sensitive coordination only.
How do I evidence encryption at rest and in transit to clients and auditors without exposing keys?
Provide vendor certification letters and audit reports, ISO 27001 and SOC 2 Type 2, and configuration screenshots showing AES 256 at rest and TLS settings for transit. Maintain a control register with system names, encryption status, and testing dates, while keeping keys managed by the platform and never shared. AI Accountant publishes encryption posture and maintains customer facing documentation you can attach to audit files.
What offboarding checklist steps must be verified for article assistants and contractors?
Disable accounts in email, storage, accounting systems, and portals, revoke MFA devices, collect laptops and tokens, remove physical access, and certify deletion of locally stored client files. Run a verification pass at day two and day seven to ensure no residual access remains. AI Accountant can trigger automated offboarding tasks and produce an offboarding certificate for the file.
How do I manage vendor due diligence for small cloud tools that do not have SOC 2 yet?
Request a completed security questionnaire, encryption details, breach history and response plan, data residency statement, and references. Contractually require DPDP clauses, audit rights, and remediation timelines. If gaps persist, ring fence the tool, restrict data categories, and plan migration to a compliant vendor. AI Accountant offers enterprise documents that can serve as a benchmark for other vendors.
What is a practical retention and deletion policy for bank statements and GST returns?
Retain only for the engagement plus statutory periods, define periods per service, for example income tax files seven to eight years as per applicable guidance, bookkeeping backups three to five years, and delete or archive securely after expiry. Maintain deletion logs and client confirmations for transparency. AI Accountant can schedule retention and trigger deletion workflows with proof of execution.
How can we run tabletop exercises without disrupting the practice, and what scenarios should we start with?
Run one hour quarterly drills, begin with a lost laptop containing bank statements, then a misdirected email with GST data, and finally a ransomware simulation. Use your RACI chart, walk through containment and communication, capture lessons learned, and update processes. AI Accountant’s incident timeline module can standardize drill documentation.
Do we need India data residency for compliance, or will strong encryption suffice for cross border tools?
Prefer India data residency for simplicity and performance. If cross border is unavoidable, strengthen safeguards, explicit consent for transfers, contractual protections, encryption at rest and in transit, and vendor breach commitments. Document transfer impact assessments. AI Accountant offers India data residency options to reduce complexity.
How do I prove consent purpose limitation when using automated bank statement ingestion?
Tie each ingestion job to a consent record specifying purpose, for example tax filing, and data category, bank statements, then enforce workflows that block processing if consent is missing or expired. Keep audit logs showing who initiated ingestion and when. AI Accountant attaches consent tokens to ingestion pipelines, which satisfy purpose limitation checks.
What KPIs should partners review monthly to ensure security posture is trending in the right direction?
Track MFA coverage, time to revoke access for departures, incidents detected and contained, consent completeness across active clients, NDA renewals due, phishing simulation click rates, and backup restore success. Review trends, act on outliers, and share wins with the team to reinforce culture. AI Accountant dashboards can surface these KPIs alongside engagement metrics.
-01%201.svg)