Key takeaways
- Fraud analytics for AP in India is a practical, high ROI defense against duplicate payments, bogus vendors, and social engineering, especially across GST and UPI heavy workflows.
- Start with basics, duplicate invoice detection, bank account change verification, and three-way matching exceptions, then scale with behavioral analytics and AI.
- Data plumbing matters, clean vendor masters, normalize Indian bank statements, and connect Tally or Zoho Books, email, and PO or GRN systems for full visibility.
- Build a review queue with maker-checker controls, clear SLAs, and documented investigations, alert quality and closure speed drive outcomes.
- Track alert, operational, and financial metrics, tune thresholds monthly, and run historical backtests to balance detection coverage with false positives.
Why Fraud Analytics for AP in India Matters Now More Than Ever
The accounts payable function has become ground zero for financial fraud in Indian businesses. Every incoming invoice could be legitimate, or it could be a sophisticated fake with a valid-looking GSTIN, crisp formatting, and believable line items. The pressure of GST compliance, month end reconciliations, and real time UPI payments amplifies risk, once funds move, recovery is rare.
Manual workflows create gaps, uploading PDFs into Tally, juggling Excel trackers, and paying through multiple bank portals invites mistakes. AI generated invoices now mimic vendor layouts, include correct HSN codes, and reference prior transactions, they look perfect at a glance. Small teams in SMBs and CA firms handle onboarding, processing, and payments, concentration of duties increases exposure across multiple clients.
Fraudsters exploit your busy hours, GST filing windows, festival periods, and payroll days, when attention drops, they strike.
[Source: Research Nester, ET BFSI, KlearStack]
India-Specific AP Fraud Patterns and Red Flags You Can't Ignore
Duplicate invoices remain rampant, vendors resubmit the same bill with minor tweaks in dates or amounts, or split amounts to bypass PO limits. Watch for same vendor, same day submissions, round amounts, or near identical line items with slightly altered headers.
Bogus vendors are more sophisticated, shell entities with stolen identities, valid looking GSTINs, and AI generated documents that pass casual checks. Red flags include frequent credit notes, mismatched GSTIN and legal names, and new vendors pushing urgent payments.
Social engineering is on the rise, imposters request bank account changes citing branch moves or upgrades, often during month end, GST rush, or holiday seasons. Spot slight domain variations, requests that bypass normal workflows, and pressure language.
Backdated invoices cluster near GSTR dates, with inconsistent HSN, sparse descriptions, or round figures that try to slip through reconciliation stress.
PO and GRN mismatches expose weak links, quantity manipulations, rate changes, and tax code alterations sneak in when exceptions get approved without evidence.
[Source: Research Nester, KlearStack, J.P. Morgan, FORVIS Mazars]
Core Controls and Analytics to Implement Today
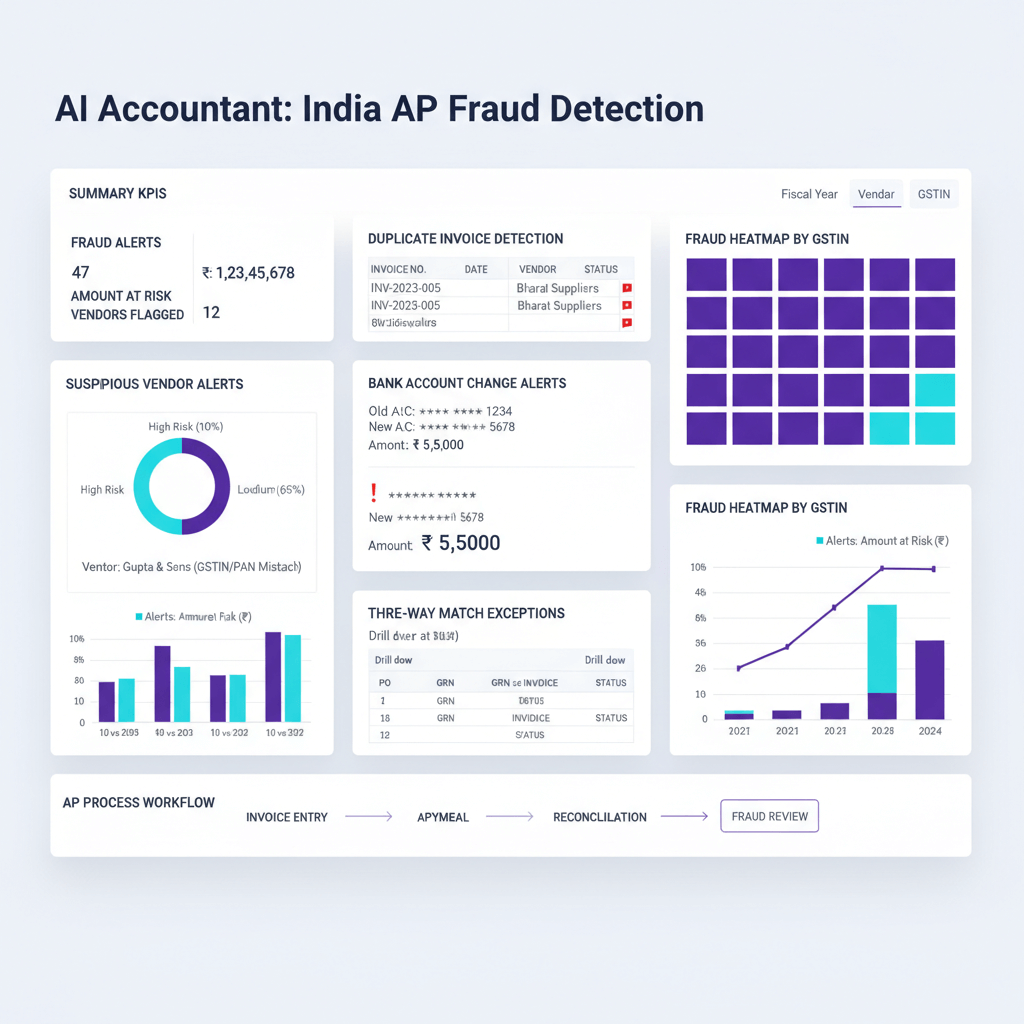
Duplicate invoice detection should combine exact and fuzzy matching, compare invoice number, date, GSTIN, vendor, amount, and line items, and set amount tolerances around 1 percent for near matches. Flag same vendor, same day patterns even if invoice numbers differ.
Suspicious vendor flags require multi layered checks, GSTIN validation, name mismatches, behavior anomalies like frequent refunds or sudden invoice velocity, and a scorecard for consistency and disputes.
Bank account change alerts are critical, enforce maker checker on beneficiary edits, require canceled cheques or bank letters, and use callback verification for high value vendors.
Three-way matching exceptions should alert on quantity, rate, tax, and terms variances, with category specific thresholds and a rule, do not auto approve small variances without review.
Review queue management centralizes triage, assign owners, set SLAs like 48 hours for high risk, maintain audit trails, and monitor false positives to refine rules.
[Source: KlearStack, FORVIS Mazars, J.P. Morgan]
Data Plumbing: What to Collect and Connect for Effective Detection
Collect structured data across bills and invoices, PO and GRN, vendor master, payment runs, and bank statements. Pull from Tally or Zoho Books, bank portals, Excel trackers, and email inboxes that carry vendor communication.
Indian bank statement formats vary widely, narrations can be cryptic or verbose. Normalizing this chaos is foundational for reliable reconciliation and anomaly detection.
Invoice layouts differ by sector, HSN fields may be missing, and amounts can be presented inconsistently. Start by cleaning your vendor master, deduplicate, standardize names, verify GSTIN and PAN, and freeze inactive records for review.
[Source: FORVIS Mazars, KlearStack, Research Nester]
Detection Logic Design That Actually Works
Duplicate logic: start with exact matches, then apply fuzzy matching for invoice numbers and amounts, check same vendor, same day pairs, and compare line item structures even if headers change. Test tolerances on six months of data, tune to balance detection and workload.
Vendor risk logic: combine rules like invalid GSTIN or multiple bank accounts per vendor with behavioral baselines for average values, frequencies, and terms. Consider ML models to pick subtle correlations as volumes grow.
Bank account changes: cross reference with historical accounts, run penny drop checks, maintain a blacklist of known bad accounts, and require independent verification.
Three-way matching: set separate quantity, rate, and tax thresholds by material and service categories, build exception hierarchies, and flag repeated small variances as a pattern.
Review operations: prioritize by value and risk, enforce segregation of duties, and record evidence, screenshots, and decisions to strengthen audit readiness.
[Source: KlearStack, Research Nester, ET BFSI, J.P. Morgan, FORVIS Mazars]
Process Playbook: From Detection to Closure
Start each day with review queue triage, assign by risk, and balance workload. Run weekly pattern reviews to find coordinated attempts. Enforce maker checker on vendor master edits, bank changes, and high value payments, and define fast escalation paths up to the CFO for critical items.
Document every step, notes, attachments, and outcomes. This plugs into modern tools, where solutions like AI Accountant support automated bill extraction, duplicates, and bank reconciliation, without disrupting Tally or Zoho Books workflows.
If it is not documented, it did not happen, audits depend on well kept trails.
[Source: FORVIS Mazars, ET BFSI, KlearStack]
Implementation Steps for an Indian CA or AP Team
- Step 1: Clean vendor master, verify GSTIN and PAN, freeze bank details, remove duplicates, and standardize names.
- Step 2: Configure thresholds, exact match for invoice number, fuzzy at 95 percent, 1 percent amount variance to start, and category based three way tolerances.
- Step 3: Build the review queue, define SLAs, assign owners, and create escalation matrices.
- Step 4: Verification scripts, penny drop, callbacks for risky vendors, and automated GSTIN checks via APIs.
- Step 5: Integrate data sources, Tally or Zoho Books, bank statements, vendor portal uploads, and email ingestion.
- Step 6: Backtest three to six months of data, measure detection and false positives, find blind spots.
- Step 7: Train the team using real cases, playbooks, and checklists.
- Step 8: Phased launch, start with high value transactions, expand as stability improves.
- Step 9: Continuous tuning, monthly thresholds, quarterly rules, annual audits.
[Source: FORVIS Mazars, KlearStack]
Essential Tools for AP Fraud Prevention
- AI Accountant, purpose built for Indian SMBs and CA firms, automates invoice processing, duplicate detection, and bank reconciliation, integrates with Tally and Zoho Books, and provides real time alert dashboards.
- QuickBooks, good for basics in duplicates and vendor management for simpler AP workflows.
- Xero, supports automated three way matching and approvals.
- FreshBooks, includes vendor tracking and bank detail change controls.
- SAP Concur, enterprise grade, with advanced analytics and AI based fraud checks.
- Zoho Expense, complements Zoho Books with expense fraud detection.
Choose based on volume, team capacity, and integration needs.
Metrics to Track and Improve Your Fraud Detection
Alert metrics, volumes by category, duplicates, vendor flags, bank changes, and three way exceptions, plus false positive rates for quality.
Operational metrics, time to detect and time to close, SLA adherence, and bottlenecks by owner or category.
Financial metrics, amounts prevented or recovered, losses avoided, and DPO impact to balance fraud controls with payment efficiency.
Vendor metrics, satisfaction, complaints on delays, and percentage under enhanced verification.
Review monthly, adjust quarterly, and align annually to strategy.
[Source: FORVIS Mazars, Payments Predictions]
Case Vignette: Real-World India-Specific Example
A Bangalore based CA firm running 500 invoices a month for a textile client catches a suspected duplicate, Rs. 2,48,500, 97 percent similar to a prior bill of Rs. 2,50,000. The AP clerk compares line items, sees matching HSN codes and descriptions, escalates, and confirms a vendor resubmission error. The payment is blocked, three hours end to end.
The same week, a bank change alert flags a new UPI ID, the email domain is one letter off, a callback to the registered number confirms no request was made. Penny drop reveals a name mismatch, the change is blocked and the UPI handle blacklisted.
Then, a three way exception shows a 10 percent rate variance on chemicals against PO, labeled as urgent delivery surcharge, not approved by procurement. The invoice is returned for correction.
Outcome: Over Rs. 8,00,000 safeguarded in a single week, the program pays for itself quickly.
[Source: Research Nester, KlearStack]
Governance and Controls for Long-Term Success
Segregation of duties is non negotiable, data entry separated from approvals, vendor edits separated from payments, and CFO oversight for high value cases. In small teams, add compensating controls like detailed documentation and surprise audits.
Vendor governance via a separate function, quarterly GSTIN revalidation, annual due diligence, and scorecards for disputes and compliance to calibrate verification levels.
Audit readiness, retain review logs, decisions, and evidence for eight years, align with SOC2 expectations, and run periodic internal audits of closed alerts.
Technology governance, access reviews, change management on thresholds and rules, and disaster recovery plans to prevent downtime exploitation.
[Source: FORVIS Mazars, ET BFSI]
Roadmap for Stronger Fraud Analytics AP India
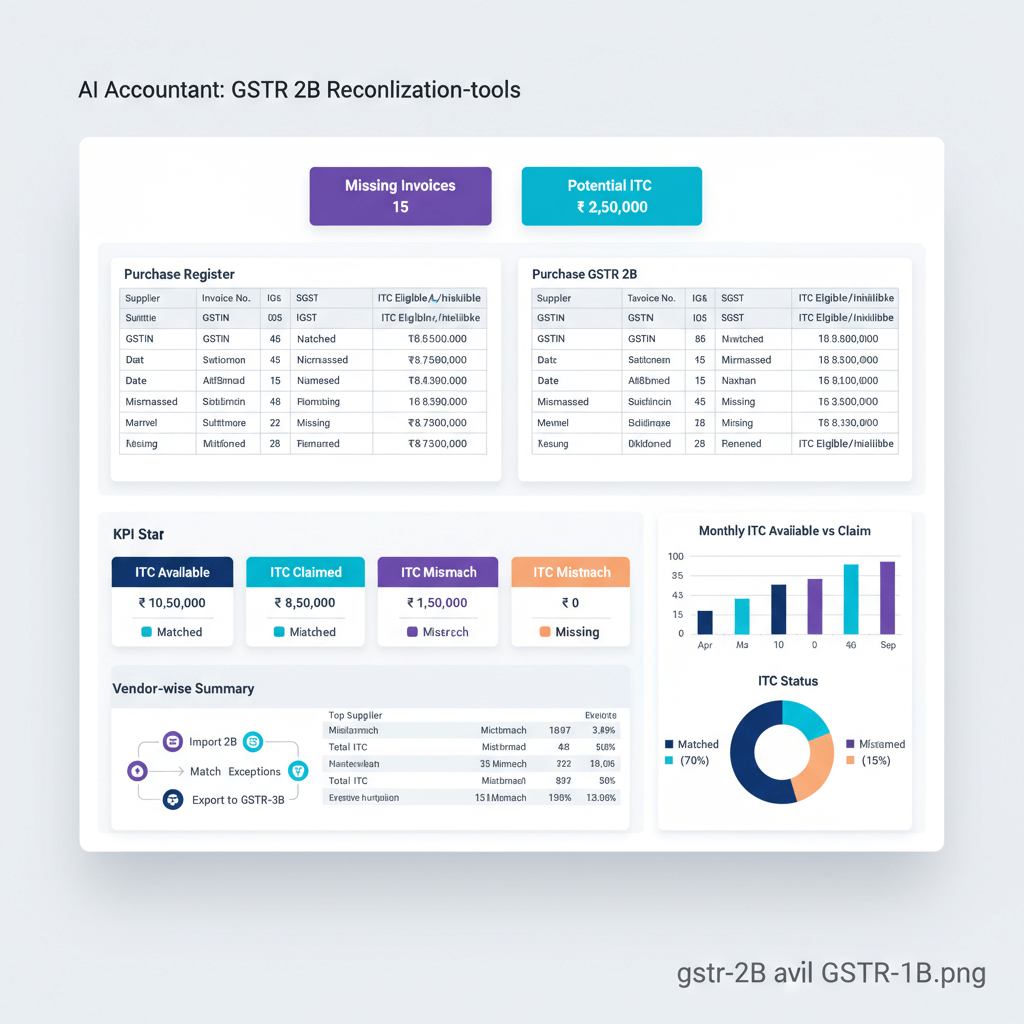
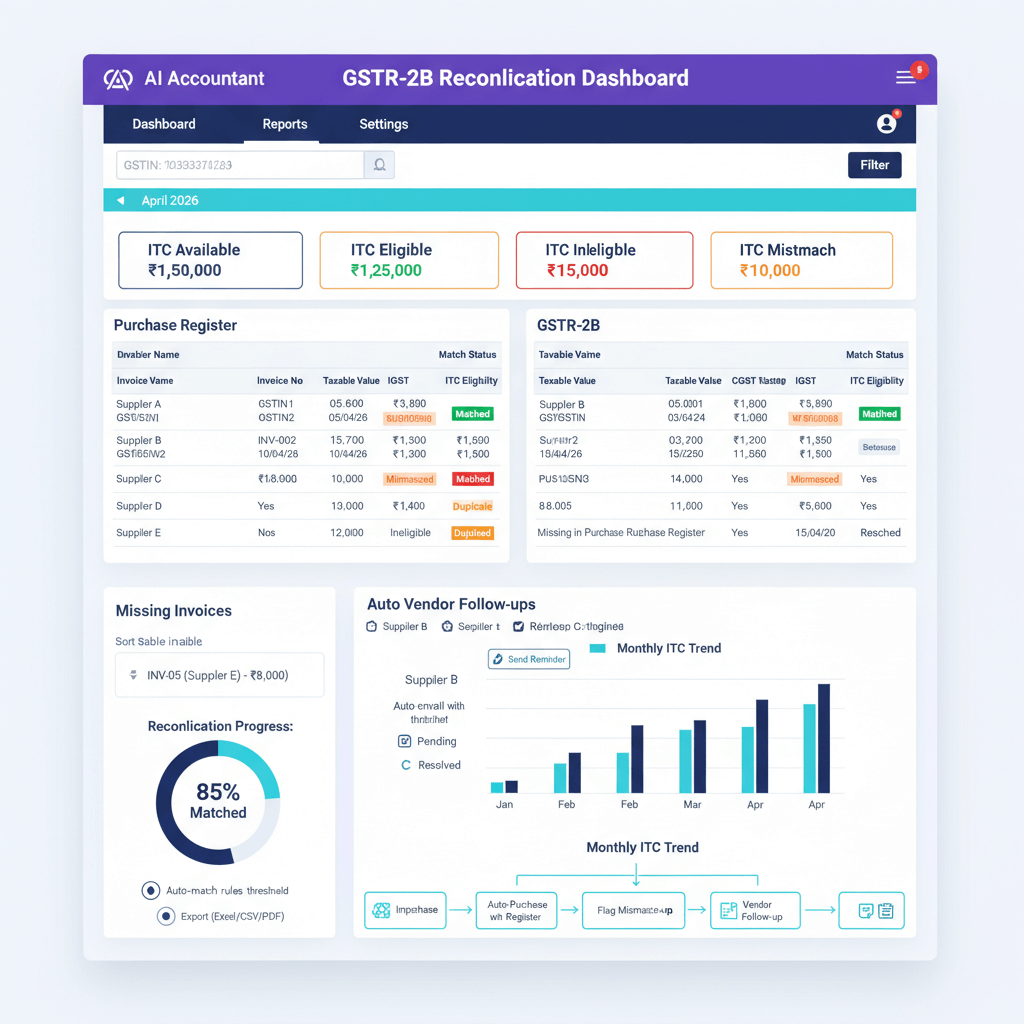
GSTN integration for real time GSTIN validation, purchase to GSTR-2B reconciliation, and discrepancy alerts from book to return.
Account Aggregator feeds for real time bank monitoring, instant payment verification, and automated reconciliation that shrinks the fraud window.
AI powered reconciliation with ML models for complex pattern detection, NLP for unstructured documents, and predictive risk scoring for pre approval checks.
Deeper integrations with ERPs, email, and verification APIs, achieving end to end visibility and faster decisions.
Blockchain may bring immutable trails and smart contract based matching as pilots mature.
[Source: Research Nester, ET BFSI, Payments Predictions]
Common Pitfalls and How to Avoid Them
- Thresholds too tight create alert fatigue, start wider, target 10 to 15 percent false positives, then tighten.
- Incomplete data wrecks detection, fix vendor masters first, enforce quality metrics and timely feeds.
- Bypassing exceptions under pressure, adopt a no payment without closure rule, record all overrides, and review next period.
- Ignoring small values invites testing, sample low value transactions and look for patterns across vendors.
- Poor cross team communication, set up a fraud committee across AP, procurement, and treasury, and share alerts.
- Weak vendor verification, go beyond GSTIN, verify PAN, bank, and address, use site or video checks for high value vendors.
- Insider threats, rotate duties, run surprise audits, monitor unusual access, and enable anonymous reporting.
[Source: FORVIS Mazars, KlearStack, J.P. Morgan]
Ready-to-Use Checklist for Implementation
Data Foundation
- [ ] Vendor master cleaned and standardized
- [ ] GSTIN validation completed for all vendors
- [ ] Bank account details verified and frozen
- [ ] Historical transaction data accessible
- [ ] Data sources integrated and tested
Detection Rules
- [ ] Duplicate invoice detection configured and tested
- [ ] Fuzzy matching thresholds set appropriately
- [ ] Suspicious vendor flags defined and activated
- [ ] GSTIN mismatch alerts operational
- [ ] Behavioral anomaly scoring implemented
Bank Account Controls
- [ ] Bank change alerts workflow documented
- [ ] Maker checker approval process enforced
- [ ] Penny drop verification operational
- [ ] Callback procedures established
- [ ] Known fraud database maintained
Three-Way Matching
- [ ] PO, GRN, Invoice thresholds configured
- [ ] Variance tolerances set by category
- [ ] Exception approval matrix defined
- [ ] Missing document alerts activated
- [ ] Tax code mismatch detection enabled
Process Framework
- [ ] Review queue live and accessible
- [ ] Alert owners assigned by category
- [ ] SLA targets defined and communicated
- [ ] Escalation matrix documented
- [ ] Investigation procedures standardized
Governance Structure
- [ ] Roles and responsibilities defined
- [ ] Segregation of duties implemented
- [ ] Audit trail requirements met
- [ ] Documentation standards established
- [ ] Training materials prepared
Monitoring and Metrics
- [ ] Dashboard for alert volumes created
- [ ] False positive tracking enabled
- [ ] Recovery reporting configured
- [ ] SLA compliance monitoring active
- [ ] Vendor satisfaction metrics defined
Testing and Training
- [ ] Historical data testing completed
- [ ] Team training sessions conducted
- [ ] Emergency procedures tested
- [ ] Escalation protocols verified
- [ ] Reference guides distributed
Conclusion: Your Path to Robust Fraud Analytics AP India
Fraud analytics AP India is about smart, scalable defenses that evolve with threats. Start with duplicate detection, prove value, then expand. Blend people, processes, and tools, and choose India aware solutions that understand GST, UPI, and local bank formats.
Share patterns with peers, keep tuning thresholds, and balance control with vendor experience. One blocked duplicate or averted bank change can repay the investment, and the peace of mind is priceless. Begin today, clean vendor data, switch on basic alerts, and stand up a simple review queue, every big fraud starts as a small undetected test.
[Source: FORVIS Mazars, Research Nester, KlearStack]
FAQ
As a CA handling multiple clients, how do I prioritize fraud analytics implementation across accounts?
Start with clients that have the highest invoice volumes, the most vendor changes, and multiple bank relationships, these concentrate risk. Implement duplicate detection and bank change verification first, then add three way matching and vendor behavior scoring. Use a common playbook, leverage an AI tool like AI Accountant to deploy templated rules across clients, and track alert quality via a shared dashboard to tune consistently.
What detection thresholds should I use initially to avoid overwhelming my AP team?
Begin with 100 percent exact invoice number match, 95 percent fuzzy match, and 1 percent amount variance for duplicates. For three way matching, set 0 to 1 percent on rates for finished goods, 3 to 5 percent on quantities for raw materials, and explicit GST variance alerts. Target 10 to 15 percent false positives in month one, review weekly, and tighten gradually. AI Accountant can simulate thresholds on historical data to find the sweet spot before go live.
How do I verify vendor bank account changes without slowing down payments?
Enforce maker checker on all beneficiary edits, run penny drop verification to confirm legal names, and perform callback verification for high value vendors using registered contacts. Automate the workflow with templated requests and evidence capture, for example, canceled cheques or bank letters attached in the review queue. Tools like AI Accountant can trigger holds until checks pass, then auto release payments.
Can I implement fraud analytics effectively if my client uses only Tally and email, without a full ERP?
Yes, connect Tally for vouchers and ledgers, ingest invoices from email, and pull bank statements in CSV or PDF. Start with duplicate detection and bank change alerts, then add lightweight three way checks using PO and GRN spreadsheets if the client lacks a full procurement module. AI Accountant integrates with Tally and email directly, enabling stepwise adoption without ERP overhauls.
How do I handle AI generated fake invoices that look legitimate with correct HSN and GST math?
Combine document level checks with cross system validation, match supplier GSTIN and PAN to government databases, verify bank details, and compare invoice line items to historical patterns. Behavioral anomalies, sudden invoice velocity or unusual discounts, often surface before format mistakes do. An AI platform like AI Accountant can fingerprint vendor layouts and flag subtle deviations, then route for human verification.
What metrics should I report to management to prove ROI on fraud analytics?
Show amounts prevented from duplicate or unauthorized payments, unresolved alert aging, false positive rate trends, and time to detect versus time to close. Include DPO impact and vendor satisfaction changes to demonstrate balance. Dashboards in AI Accountant consolidate these KPIs, making monthly and quarterly reviews simple and credible.
How can I reduce false positives without missing real fraud attempts?
Segment thresholds by category, vendor tier, and transaction value, and use multi factor rules, for instance, flag duplicates only when fuzzy match plus same day submission both occur. Backtest on six months of data, remove noisy fields, and adjust tolerances where precision suffers. AI Accountant supports behavioral baselining per vendor, which reduces noise while keeping sensitivity to outliers.
What are practical controls for SMBs where full segregation of duties is not possible?
Use compensating controls, documented self approvals, periodic rotation of responsibilities, surprise audits, and mandatory callback verification for exceptions. Implement a review queue where a different person reviews alerts, even if the same person enters vouchers. AI Accountant can enforce maker checker digitally, capturing evidence and approvals for audit comfort.
How do I manage fraud risk during GST filing rush or festival seasons when the team is stretched?
Pre lock high risk controls, auto hold bank account changes, raise sensitivity on duplicates, and enforce stricter SLAs for high value invoices. Schedule staggered review shifts, pre validate vendor masters, and run quick health checks the week before filings. AI Accountant can auto escalate critical alerts and throttle low risk ones to keep capacity focused where it matters.
What data do I absolutely need to get started, and what can wait for phase two?
Must haves, vendor master with GSTIN, PAN, bank details, invoices with numbers, dates, amounts, GST breakdown, and bank statements. Phase two, PO and GRN integration, email ingestion for vendor communications, and behavioral baselines. Start with clean vendor masters and payment data, then layer in PO or GRN for three way matching as process maturity improves, AI Accountant supports this phased approach.
How should I treat small value transactions, do I really need to scan them?
Yes, sample small values regularly, fraudsters often test controls with minor amounts. Use rules that batch low value alerts for periodic review, and leverage pattern detection across vendors to spot distributed leakage. AI Accountant can group micro alerts into pattern based flags, reducing workload while preserving coverage.
What evidence should I store for audit readiness when closing alerts?
Keep investigator notes, matched documents, screenshots of emails or portals, verification proofs like penny drop confirmations, callback logs, and final decisions with timestamps. Maintain trails for at least eight years to align with Indian requirements. A tool like AI Accountant automatically timestamps actions, ties artefacts to alerts, and exports audit packs on demand.
-01%201.svg)